What is Firewall
What does the firewall do
Firewalls and network security
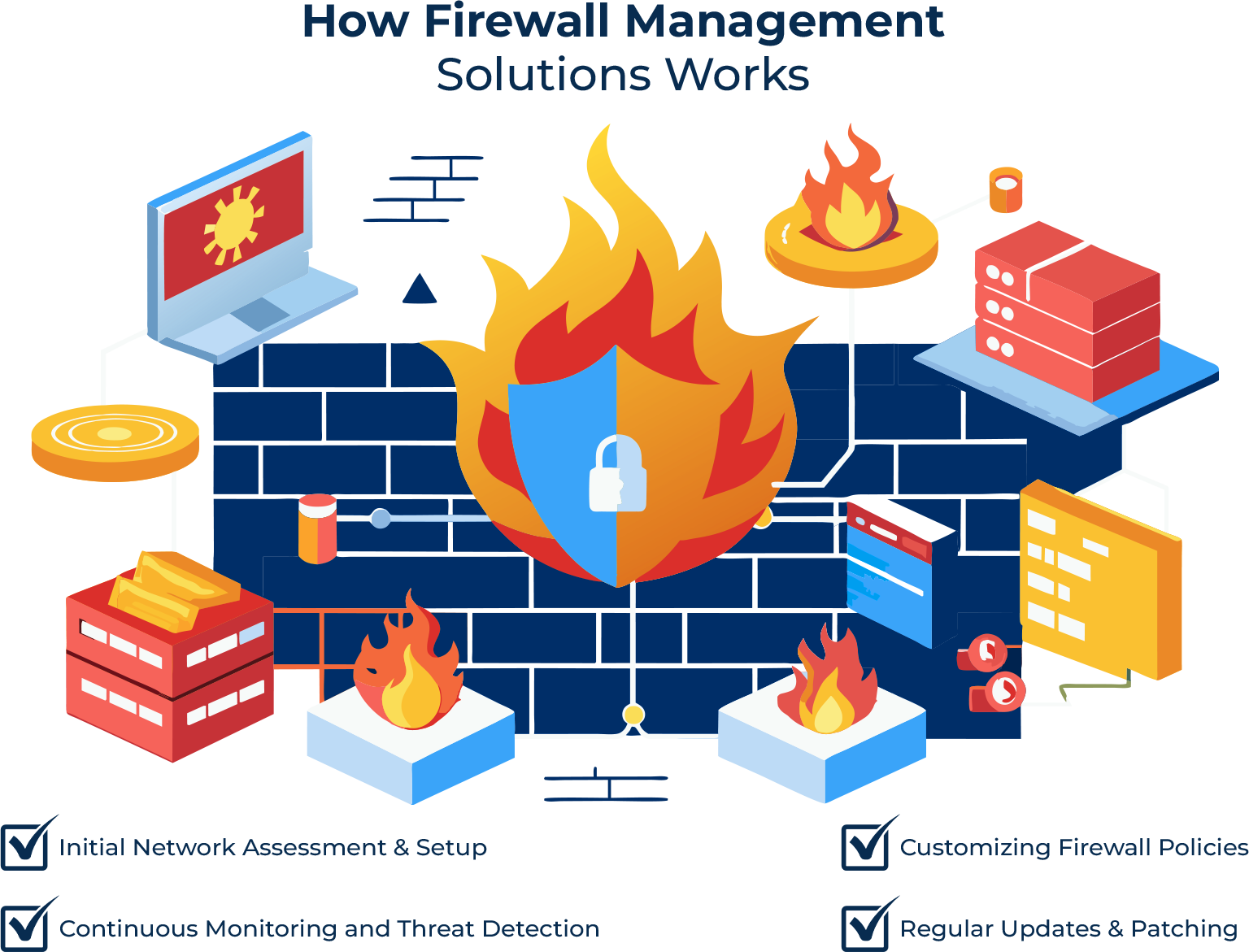
How Firewall Management Solutions Work
At Netraclouds, our firewall management process is designed to be seamless, comprehensive, and proactive. From initial setup to continuous monitoring and updates, we ensure that your network remains secure at all times. TinyWall offers a free, secure, and non-intrusive firewall solution for Windows users.
Here’s how our firewall management solutions work:
1. Initial Network Assessment and Setup
The first step in our firewall management process is a thorough network assessment. Our experts analyze your current network infrastructure, identify potential vulnerabilities, and understand your specific security needs. Based on this assessment, we recommend the best network firewall protection tailored to your organization.
.
Customized Solution Development: We design a tailored firewall strategy that fits your network architecture, business goals, and specific security needs.
2. Customizing Firewall Policies
Once the firewall is installed, we create tailored security policies to ensure your network’s protection is both efficient and effective. These policies define rules for how your network interacts with external traffic, controlling access and blocking malicious activity.
Access Control Rules: We set policies to control who and what can access your network resources, both internally and externally.
Traffic Filtering: We implement rules to filter traffic based on predefined parameters, ensuring that only legitimate data is allowed to pass through.
3. Continuous Monitoring and Threat Detection
Our firewall management system includes real-time monitoring, which constantly scans for potential security threats. Our team keeps a close eye on your network 24/7, providing instant response to any detected anomalies or breaches.
Automated Threat Detection: Our system automatically identifies and blocks threats like malware, viruses, and intrusions before they reach your network.
Real-Time Monitoring: We continuously track network traffic, allowing us to spot unusual behavior and take immediate action.
4. Regular Updates and Patching
Firewalls need to be updated regularly to stay ahead of evolving threats. We make sure your firewall system stays current by applying the latest security patches, updates, and enhancements.
Types of Firewalls
Packet-Filtering Firewall: Inspects data packets based on predefined rules, such as IP addresses and ports. It’s simple but lacks deep inspection.
Stateful Inspection Firewall: Tracks the state of active connections and evaluates traffic based on connection state, offering more security than packet filtering.
Proxy Firewall: Acts as an intermediary between users and the internet, filtering traffic and hiding internal network details for added security.
Next-Generation Firewall (NGFW): Combines traditional firewall features with advanced capabilities like deep packet inspection, intrusion prevention, and application awareness.
Web Application Firewall (WAF): This type of firewall protects web applications by filtering and monitoring HTTP traffic to prevent common web-based attacks.
Circuit-Level Gateway Firewall: Works at the session layer, monitoring the TCP handshake process to validate connections.
Software Firewall: Installed on individual devices to protect them from external threats.
Hardware Firewall: A physical device that protects entire network protection hardware by filtering traffic at the perimeter.
Features of Our Firewall Management Services
1. 24/7 Monitoring and Support
2. Automated Threat Detection:
3. Real-Time Alerts and Reporting:
4. Customizable Security Policies:
5. Seamless Integration
5. Secure VPN and Remote Access
6. Ongoing Updates and Patching:
Benefits of Firewall Services
Ready to safeguard your network?
Contact us today to learn more about our best-in-class firewall management solutions and how we can help you enhance your security infrastructure.
Conclusion:
Frequently Asked Question
Firewall management involves configuring, monitoring, and maintaining firewall systems to protect networks from unauthorized access, cyber threats, and data breaches.
It ensures continuous protection, minimizes vulnerabilities, enforces security policies, and helps organizations comply with data protection regulations.
Key features include centralized management, real-time monitoring, threat detection, automation, policy management, reporting, and compliance support.
Yes. Many solutions offer cloud-based platforms that allow centralized control of on-premise and cloud firewalls from a single dashboard.
Evaluate based on your network size, security needs, budget, and compatibility with existing infrastructure. Consider vendor reputation and support quality.



